一、組網及說明
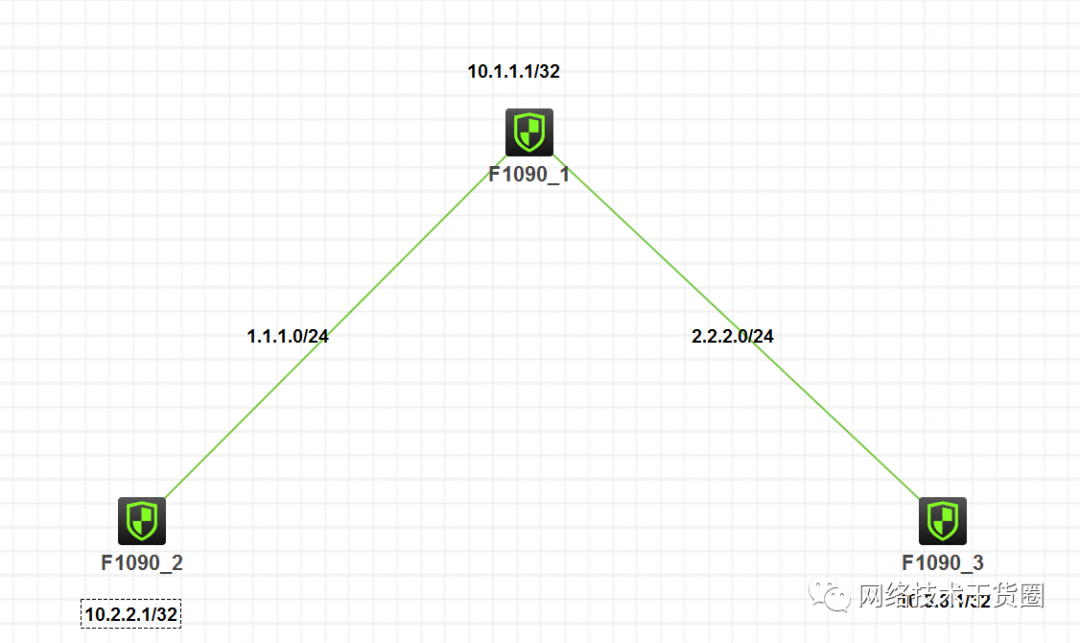
注:如無特別說明,描述中的 FW1 或 MSR1 對應拓撲中設備名稱末尾數字為 1 的設備,FW2 或 MSR2 對應拓撲中設備名稱末尾數字為 2 的設備,以此類推;另外,同一網段中,IP 地址的主機位為其設備編號,如 FW1 的 g0/0 接口若在 1.1.1.0/24 網段,則其 IP 地址為 1.1.1.1/24,以此類推。
二、實驗需求
FW1代表中心節點,FW2和FW3代表分支。
分支分別和中心節點通信,各分支節點之間可以相互通信。
三、配置步驟
3.1 IP、路由、安全域
FW1
# interfaceLoopBack0 ipaddress10.1.1.1255.255.255.255 # interfaceGigabitEthernet1/0/1 portlink-moderoute comboenablecopper ipaddress2.2.2.1255.255.255.0 ipsecapplypolicyply # security-zonenameLocal # security-zonenameTrust importinterfaceGigabitEthernet1/0/0 importinterfaceGigabitEthernet1/0/1 # iproute-static10.2.2.1321.1.1.2 iproute-static10.3.3.1322.2.2.3 # security-policyip rule0nameany actionpass
FW2
# interfaceLoopBack0 ipaddress10.2.2.1255.255.255.255 # interfaceGigabitEthernet1/0/0 portlink-moderoute comboenablecopper ipaddress1.1.1.2255.255.255.0 ipsecapplypolicyply # security-zonenameLocal # security-zonenameTrust importinterfaceGigabitEthernet1/0/0 importinterfaceGigabitEthernet1/0/1 # iproute-static0.0.0.001.1.1.1 # security-policyip rule0nameany actionpass
FW3
# interfaceLoopBack0 ipaddress10.3.3.1255.255.255.0 # interfaceGigabitEthernet1/0/0 portlink-moderoute comboenablecopper ipaddress2.2.2.3255.255.255.0 ipsecapplypolicyply # security-zonenameLocal # security-zonenameTrust importinterfaceGigabitEthernet1/0/0 importinterfaceGigabitEthernet1/0/1 # iproute-static0.0.0.002.2.2.1 # security-policyip rule0nameany actionpass #
3.2 IKE部分
FW1
# ikekeychaink1 pre-shared-keyhostnamef2keycipher$c$3$rFTHo6O4pPLOHvZEwmSFGc3gjFRY7Q75Qw== # ikekeychaink2 pre-shared-keyhostnamef3keycipher$c$3$lo0leXtmx41UHB7Vxok9kFeOJxZnJZ0miw== # ikeprofilepf keychaink1 keychaink2 dpdinterval10on-demand exchange-modeaggressive local-identityfqdnf1 matchremoteidentityfqdnf2 matchremoteidentityfqdnf3
FW2
# ikekeychaink1 pre-shared-keyaddress1.1.1.1255.255.255.255keycipher$c$3$v44JHWonfkj3w9BqDNkQ+LEIFRiUlBKUgw== # ikeprofilepf keychaink1 exchange-modeaggressive local-identityfqdnf2 matchremoteidentityfqdnf1
FW3
# ikekeychaink1 pre-shared-keyaddress2.2.2.1255.255.255.255keycipher$c$3$PKsnAPnnOgZicN73gXZd3L3ZO9OR3IuS1A== # ikeprofilepf keychaink1 exchange-modeaggressive local-identityfqdnf3 matchremoteidentityfqdnf1
3.3 IPsec部分
FW1
# acladvanced3000 rule0permitipsource10.1.1.10destination10.2.2.10 rule5permitipsource10.1.1.10destination10.3.3.10 rule10permitipsource10.3.3.10destination10.2.2.10 rule15permitipsource10.2.2.10destination10.3.3.10 # ipsectransform-setts espencryption-algorithm3des-cbc espauthentication-algorithmmd5 # ipsecpolicy-templatept1 transform-setts securityacl3000 ike-profilepf # ipsecpolicyply1isakmptemplatept
FW2
# acladvanced3000 rule0permitipsource10.2.2.10destination10.1.1.10 rule5permitipsource10.2.2.10destination10.3.3.10 # ipsectransform-setts espencryption-algorithm3des-cbc espauthentication-algorithmmd5 # ipsecpolicyply1isakmp transform-setts securityacl3000 remote-address1.1.1.1 ike-profilepf
FW3
# acladvanced3000 rule0permitipsource10.3.3.10destination10.1.1.10 rule5permitipsource10.3.3.10destination10.2.2.10 # ipsectransform-setts espencryption-algorithm3des-cbc espauthentication-algorithmmd5 # ipsecpolicyply1isakmp transform-setts securityacl3000 remote-address2.2.2.1 ike-profilepf
四、配置關鍵點
分支和中心節點之間的隧道建立要通過分支來觸發,即FW2向FW1發起訪問,FW3向FW1發起訪問。
分支和分支之間建立隧道需要兩邊觸發,即FW2向FW3發起訪問,FW3向FW2發起訪問。
分支的感興趣流除了目的是中心節點外,還需要包括到分支的。
FW1上的ipsec sa如下:
------------------------------- Interface:GigabitEthernet1/0/0 ------------------------------- ----------------------------- IPsecpolicy:ply Sequencenumber:1 Mode:Template ----------------------------- Tunnelid:1 Encapsulationmode:tunnel PerfectForwardSecrecy: InsideVPN: ExtendedSequenceNumbersenable:N TrafficFlowConfidentialityenable:N Transmittingentity:Responder PathMTU:1444 Tunnel: localaddress:1.1.1.1 remoteaddress:1.1.1.2 Flow: souraddr:10.1.1.1/255.255.255.255port:0protocol:ip destaddr:10.2.2.1/255.255.255.255port:0protocol:ip [InboundESPSAs] SPI:3754823141(0xdfce0de5) ConnectionID:4294967298 Transformset:ESP-ENCRYPT-3DES-CBCESP-AUTH-MD5 SAduration(kilobytes/sec):1843200/3600 SAremainingduration(kilobytes/sec):1843199/3562 Maxreceivedsequence-number:4 Anti-replaycheckenable:Y Anti-replaywindowsize:64 UDPencapsulationusedforNATtraversal:N Status:Active [OutboundESPSAs] SPI:1056998950(0x3f008626) ConnectionID:4294967299 Transformset:ESP-ENCRYPT-3DES-CBCESP-AUTH-MD5 SAduration(kilobytes/sec):1843200/3600 SAremainingduration(kilobytes/sec):1843199/3562 Maxsentsequence-number:4 UDPencapsulationusedforNATtraversal:N Status:Active ----------------------------- IPsecpolicy:ply Sequencenumber:1 Mode:Template ----------------------------- Tunnelid:2 Encapsulationmode:tunnel PerfectForwardSecrecy: InsideVPN: ExtendedSequenceNumbersenable:N TrafficFlowConfidentialityenable:N Transmittingentity:Responder PathMTU:1444 Tunnel: localaddress:1.1.1.1 remoteaddress:1.1.1.2 Flow: souraddr:10.3.3.1/255.255.255.255port:0protocol:ip destaddr:10.2.2.1/255.255.255.255port:0protocol:ip [InboundESPSAs] SPI:3260450656(0xc2568760) ConnectionID:4294967300 Transformset:ESP-ENCRYPT-3DES-CBCESP-AUTH-MD5 SAduration(kilobytes/sec):1843200/3600 SAremainingduration(kilobytes/sec):1843199/3575 Maxreceivedsequence-number:8 Anti-replaycheckenable:Y Anti-replaywindowsize:64 UDPencapsulationusedforNATtraversal:N Status:Active [OutboundESPSAs] SPI:2013923382(0x780a0836) ConnectionID:4294967301 Transformset:ESP-ENCRYPT-3DES-CBCESP-AUTH-MD5 SAduration(kilobytes/sec):1843200/3600 SAremainingduration(kilobytes/sec):1843199/3575 Maxsentsequence-number:5 UDPencapsulationusedforNATtraversal:N Status:Active ------------------------------- Interface:GigabitEthernet1/0/1 ------------------------------- ----------------------------- IPsecpolicy:ply Sequencenumber:1 Mode:Template ----------------------------- Tunnelid:0 Encapsulationmode:tunnel PerfectForwardSecrecy: InsideVPN: ExtendedSequenceNumbersenable:N TrafficFlowConfidentialityenable:N Transmittingentity:Responder PathMTU:1444 Tunnel: localaddress:2.2.2.1 remoteaddress:2.2.2.3 Flow: souraddr:10.1.1.1/255.255.255.255port:0protocol:ip destaddr:10.3.3.1/255.255.255.255port:0protocol:ip [InboundESPSAs] SPI:2022161426(0x7887bc12) ConnectionID:4294967296 Transformset:ESP-ENCRYPT-3DES-CBCESP-AUTH-MD5 SAduration(kilobytes/sec):1843200/3600 SAremainingduration(kilobytes/sec):1843199/3554 Maxreceivedsequence-number:4 Anti-replaycheckenable:Y Anti-replaywindowsize:64 UDPencapsulationusedforNATtraversal:N Status:Active [OutboundESPSAs] SPI:3633752750(0xd896aaae) ConnectionID:4294967297 Transformset:ESP-ENCRYPT-3DES-CBCESP-AUTH-MD5 SAduration(kilobytes/sec):1843200/3600 SAremainingduration(kilobytes/sec):1843199/3554 Maxsentsequence-number:4 UDPencapsulationusedforNATtraversal:N Status:Active ----------------------------- IPsecpolicy:ply Sequencenumber:1 Mode:Template ----------------------------- Tunnelid:3 Encapsulationmode:tunnel PerfectForwardSecrecy: InsideVPN: ExtendedSequenceNumbersenable:N TrafficFlowConfidentialityenable:N Transmittingentity:Responder PathMTU:1444 Tunnel: localaddress:2.2.2.1 remoteaddress:2.2.2.3 Flow: souraddr:10.2.2.1/255.255.255.255port:0protocol:ip destaddr:10.3.3.1/255.255.255.255port:0protocol:ip [InboundESPSAs] SPI:3168528224(0xbcdbe760) ConnectionID:4294967302 Transformset:ESP-ENCRYPT-3DES-CBCESP-AUTH-MD5 SAduration(kilobytes/sec):1843200/3600 SAremainingduration(kilobytes/sec):1843199/3583 Maxreceivedsequence-number:5 Anti-replaycheckenable:Y Anti-replaywindowsize:64 UDPencapsulationusedforNATtraversal:N Status:Active [OutboundESPSAs] SPI:2761355159(0xa496ef97) ConnectionID:4294967303 Transformset:ESP-ENCRYPT-3DES-CBCESP-AUTH-MD5 SAduration(kilobytes/sec):1843200/3600 SAremainingduration(kilobytes/sec):1843199/3583 Maxsentsequence-number:5 UDPencapsulationusedforNATtraversal:N Status:Active
實驗結束!
審核編輯:劉清
-
IPSec
+關注
關注
0文章
59瀏覽量
22808 -
MSR
+關注
關注
0文章
18瀏覽量
8001
原文標題:H3C實驗 | 通過IPsec野蠻模式實現分支之間相互通信
文章出處:【微信號:網絡技術干貨圈,微信公眾號:網絡技術干貨圈】歡迎添加關注!文章轉載請注明出處。
發布評論請先 登錄
相關推薦
工廠有多臺PLC時,不同網段之間如何實現相互訪問?

ipsec組網通過其加密和驗證機制提供高安全性
IPSec VPN解決方案讓遠程辦公更加輕松可靠




 怎樣通過IPsec野蠻模式實現分支之間相互通信呢
怎樣通過IPsec野蠻模式實現分支之間相互通信呢









評論