usbrip取證工具
usbrip(源自"USB Ripper",而不是"USB RIP")是一個帶有CLI界面的開源取證工具,可以讓您在Linux機器上跟蹤USB設備(即USB事件歷史記錄,"已連接"和"已斷開連接"事件)。
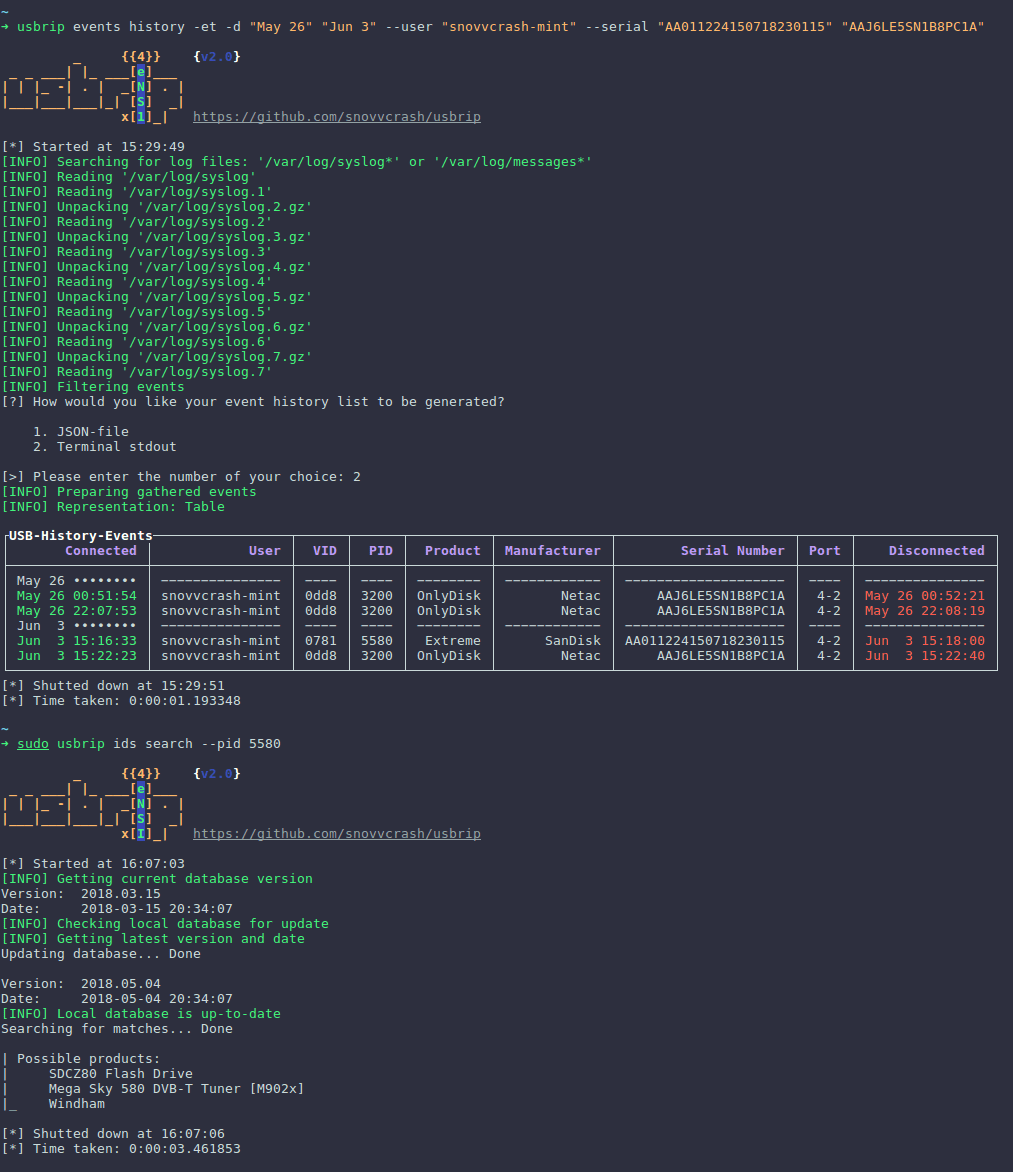

usbrip是用Python3編寫的軟件,它解析Linux日志文件
/var/log/syslog* 或 /var/log/messages*
以構建USB事件歷史表。
此類表格可能包含以下列:
"已連接"(日期和時間),
"用戶",
"VID"(供應商ID),
"產品",
"制造商",
"序列號",
"端口"和
"斷開連接"(日期和時間)。
此外,它還可以:
(1).導出收集的信息作為JSON轉儲;
(2).生成一個授權(可信)USB設備列表作為JSON(稱之為auth.json);
(3).根據以下內容搜索(違規事件)auth.json:show(或生成另一個JSON)USB設備出現在歷史記錄中并且不會出現在auth.json;
(4).*使用-sflag * 安裝時,創建加密存儲(7zip存檔),以便在crontab調度程序的幫.助下自動備份和累積USB事件;
(5).根據其VID和/或PID搜索有關特定USB設備的其他詳細信息。
usbrip安裝
快速安裝
usbrip可在PyPI下載和安裝:
$ pip3 install usbrip
git安裝
# 下載 ~$ git clone https://github.com/snovvcrash/usbrip.git usbrip && cd usbrip ~/usbrip$ # 安裝依賴 ~$ sudo apt install python3-venv p7zip-full -y
有兩種方法,可以將usbrip安裝到系統中:
pip或setup.py。
pip要么setup.py
首先,usbrip是通過pip安裝的。這意味著在git克隆了repo之后可以簡單地啟動pip安裝過程,然后在終端的任何地方運行usbrip,如下所示:
~/usbrip$ python3 -m venv venv && source venv/bin/activate (venv) ~/usbrip$ pip install . (venv)~/usbrip$usbrip-h
或者,如果要在本地解析Python依賴關系(不打擾PyPI),請使用setup.py
~/usbrip$ python3 -m venv venv && source venv/bin/activate (venv) ~/usbrip$ python setup.py install (venv)~/usbrip$usbrip-h
注意:
您可能希望在Python虛擬環境處于活動狀態時運行安裝過程(如上所示)
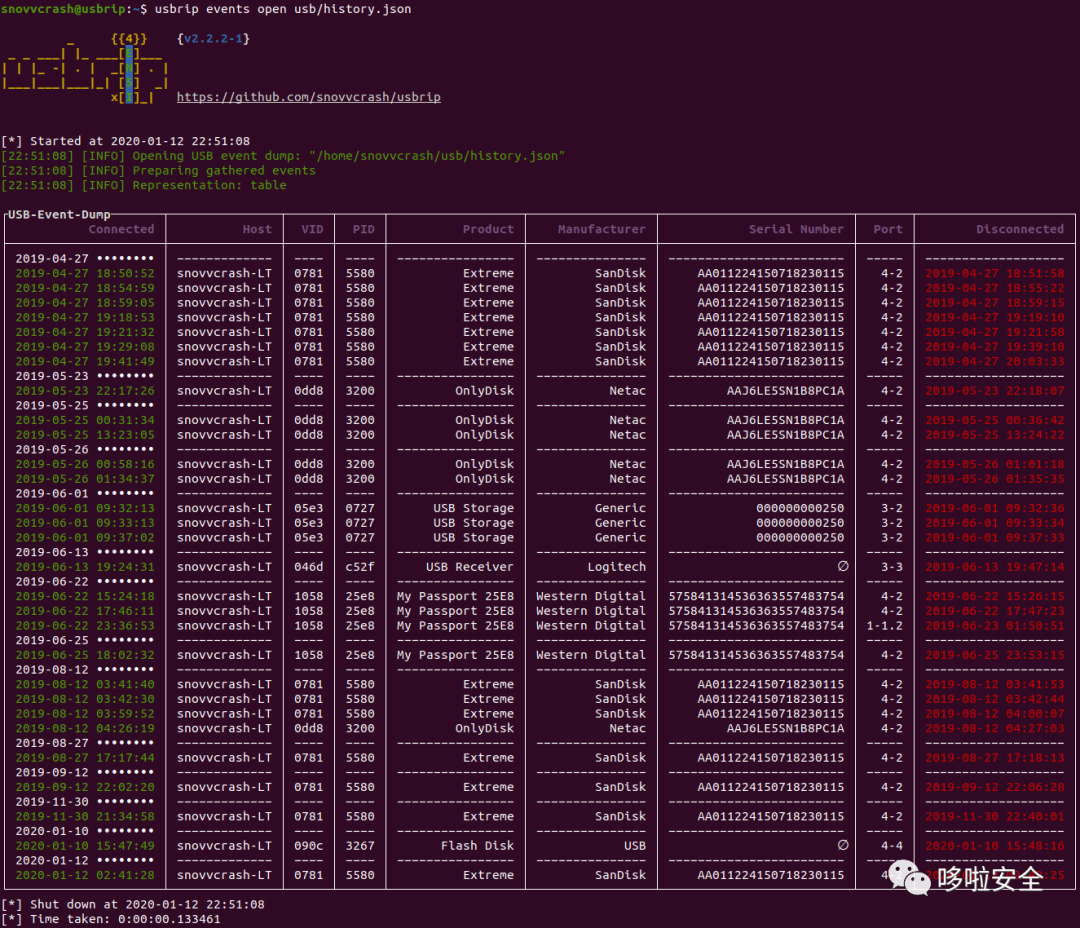
usbrip使用
# ---------- BANNER ---------- $ usbrip banner Get usbrip banner. # ---------- EVENTS ---------- $ usbrip events history [-t | -l] [-e] [-n] [-d [ ...]] [--user [ ...]] [--vid [ ...]] [--pid [ ...]] [--prod [ ...]] [--manufact [ ...]] [--serial [ ...]] [--port [ ...]] [-c [ ...]] [-f [ ...]] [-q] [--debug] Get USB event history. $ usbrip events open [-t | -l] [-e] [-n ] [-d [ ...]] [--user [ ...]] [--vid [ ...]] [--pid [ ...]] [--prod [ ...]] [--manufact [ ...]] [--serial [ ...]] [--port [ ...]] [-c [ ...]] [-f [ ...]] [-q] [--debug] Open USB event dump. $ usbrip events gen_auth [-a [ ...]] [-e] [-n ] [-d [ ...]] [--user [ ...]] [--vid [ ...]] [--pid [ ...]] [--prod [ ...]] [--manufact [ ...]] [--serial [ ...]] [--port [ ...]] [-f [ ...]] [-q] [--debug] Generate a list of trusted (authorized) USB devices. $ usbrip events violations [-a [ ...]] [-t | -l] [-e] [-n ] [-d [ ...]] [--user [ ...]] [--vid [ ...]] [--pid [ ...]] [--prod [ ...]] [--manufact [ ...]] [--serial [ ...]] [--port [ ...]] [-c [ ...]] [-f [ ...]] [-q] [--debug] Get USB violation events based on the list of trusted devices. # ---------- STORAGE ---------- $ usbrip storage list [-q] [--debug] List contents of the selected storage (7zip archive). STORAGE_TYPE is "history" or "violations". $ usbrip storage open [-t | -l] [-e] [-n ] [-d [ ...]] [--user [ ...]] [--vid [ ...]] [--pid [ ...]] [--prod [ ...]] [--manufact [ ...]] [--serial [ ...]] [--port [ ...]] [-c [ ...]] [-q] [--debug] Open selected storage (7zip archive). Behaves similary to the EVENTS OPEN submodule. $ usbrip storage update [-a [ ...]] [-e] [-n ] [-d [ ...]] [--user [ ...]] [--vid [ ...]] [--pid [ ...]] [--prod [ ...]] [--manufact [ ...]] [--serial [ ...]] [--port [ ...]] [--lvl ] [-q] [--debug] Update storage — add USB events to the existing storage (7zip archive). COMPRESSION_LEVEL is a number in [0..9]. $ usbrip storage create [-a [ ...]] [-e] [-n ] [-d [ ...]] [--user [ ...]] [--vid [ ...]] [--pid [ ...]] [--prod [ ...]] [--manufact [ ...]] [--serial [ ...]] [--port [ ...]] [--lvl ] [-q] [--debug] Create storage — create 7zip archive and add USB events to it according to the selected options. $ usbrip storage passwd [--lvl ] [-q] [--debug] Change password of the existing storage. # ---------- IDs ---------- $ usbrip ids search [--vid ] [--pid ] [--offline] [-q] [--debug] Get extra details about a specific USB device by its and/or from the USB ID database. $ usbrip ids download [-q] [--debug] Update (download) the USB ID database.
usbrip的使用示例
顯示所有USB設備的事件歷史
$ usbrip events history -ql -n 100
顯示外部USB設備的事件歷史
$ usbrip events history -et -c conn vid pid disconn serial -d "Dec 9" "Dec 10" -f /var/log/syslog.1 /var/log/syslog.2.gz
審核編輯:劉清
-
USB設備
+關注
關注
0文章
57瀏覽量
16331 -
LINUX內核
+關注
關注
1文章
316瀏覽量
21644 -
GNU
+關注
關注
0文章
143瀏覽量
17492 -
CLI
+關注
關注
1文章
79瀏覽量
8541
原文標題:GNU/Linux上跟蹤USB設備的取證工具
文章出處:【微信號:哆啦安全,微信公眾號:哆啦安全】歡迎添加關注!文章轉載請注明出處。
發布評論請先 登錄
相關推薦
Linux內核開發工具介紹
Linux系統爭議——是Linux還是GNU/Linux?
介紹一款蘋果操作系統的電源管理工具
一款VScode的插件介紹
一款國產USB3.0HUB集線器芯片
Linux下GNU Radio平臺的搭建以及該如何使用NI USRP設備
Linux下的硬件驅動—USB設備(上)
AutoGadgetFS:一款針對USB設備的安全測試工具
介紹一款基于go的windows信息收集工具
介紹一款有源濾波器的設計工具
GNU/Linux和Linux的區別在哪?
初識內存取證-volatility與Easy_dump
一款運行于windows上的linux命令神器-Cmder




 介紹一款GNU/Linux上跟蹤USB設備的取證工具
介紹一款GNU/Linux上跟蹤USB設備的取證工具









評論