一、H3C Router配置:
system-view//進入配置模式
[H3CRouter]local-user admin//添加本地用戶
[H3CRouter-luser-cisco]password simple admin//為添加的用戶設置密碼
[H3CRouter-luser-cisco]service-type web//開啟網頁配置功能
[H3CRouter-luser-cisco]quit
[H3CRouter]Ethernetinterface Ethernet 0/0//進入接口配置模式
[H3CRouter-Ethernet0/0]ip address 123.15.36.140 255.255.255.128//配置外網接口地址
[H3CRouter-Ethernet0/0]quit//退出接口配置模式
[H3CRouter-Ethernet0/1]ip address 172.18.253.1 255.255.255.0//配置內外接口地址
[H3CRouter-Ethernet0/0]quit//退出接口配置模式
[H3CRouter]ip route-static 0.0.0.0 0.0.0.0 123.15.36.129//配置靜態路由
[H3CRouter]acl number 3000//創建訪問控制列表
[H3CRouter-acl-3000]rule 5 permit ip source 172.18.253.0 0.0.0.255//允許內網網段訪問公網
[H3CRouter-Ethernet0/0]quit//退出接口配置模式
[H3CRouter]acl number 3001//創建訪問控制列表
[H3CRouter-acl-3001]rule 0 permit ip source 172.18.253.0 0.0.0.255 destination 192.168.0.0 0.0.255.255
rule 5 deny ip//拒絕除內網網段以為的網段訪問遠端子網
[H3CRouter]Ethernetinterface Ethernet 0/0//進入接口配置模式
[H3CRouter-Ethernet0/0]nat outbound 3000//在外網接口上啟用ACL 3000
[H3CRouter-Ethernet0/0]quit//退出接口配置模式
[H3CRouter]ike proposal 1//創建IKE提議,并進入IKE提議視圖
[H3CRouter]ike peer fenzhi//創建一個IKE對等體,并進入IKE-Peer視圖
[H3CRouter-ike-peer-fenzhi]exchange-mode aggressive//配置IKE第一階段的協商為野蠻模式
[H3CRouter-ike-peer-fenzhi]proposal 1//配置IKE對等體引用的IKE安全提議
[H3CRouter-ike-peer-fenzhi]pre-shared-key simple abc123//配置采用預共享密鑰認證時,所使用的預共享密鑰
[H3CRouter-ike-peer-fenzhi]id-type name//選擇IKE第一階段的協商過程中使用ID的類型
[H3CRouter-ike-peer-fenzhi]remote-name fenzhi//配置對端安全網關的名字
[H3CRouter-ike-peer-fenzhi]remote-address fenzhi dynamic//配置對端安全網關的IP地址
[H3CRouter-ike-peer-fenzhi]local-address 123.15.36.140//配置本端安全網關的IP地址
H3CRouter-ike-peer-fenzhi]local-name center//配置本端安全網關的名字
[H3CRouter-ike-peer-fenzhi]nat traversal//配置IKE/IPsec的NAT穿越功能
[H3CRouter-ike-peer-fenzhi]quit
[H3CRouter]ipsec transform-set fenzhi//配置IPsec安全提議fenzhi
[H3CRouter-ipsec-transform-set-tran1]encapsulation-mode tunnel//報文封裝形式采用隧道模式
[H3CRouter-ipsec-transform-set-tran1]transform esp//安全協議采用ESP協議
[H3CRouter-ipsec-transform-set-tran1]esp encryption-algorithm 3des//選擇ESP協議采用的加密算法
[H3CRouter-ipsec-transform-set-tran1]esp authentication-algorithm md5//選擇ESP協議采用的認證算法
[H3CRouter-ipsec-transform-set-tran1]quit
[H3CRouter]ipsec policy 983040 1 isakmp//創建一條IPsec安全策略,協商方式為isakmp
[H3CRouter-ipsec-policy-isakmp-use1-10]security acl 3001//引用訪問控制列表3001
[H3CRouter-ipsec-policy-isakmp-use1-10]transform-set fenzhi//引用IPsec安全提議
[H3CRouter-ipsec-policy-isakmp-use1-10]ike-peer fenzhi//引用IKE對等體
[H3CRouter-ipsec-policy-isakmp-use1-10]quit
[H3CRouter]interface ethernet 0/0//進入外部接口
[H3CRouter-Ethernet0/1]ipsec policy 983040//在外部接口上應用IPsec安全策略組
驗證配置結果
[H3CRouter]display ike proposal
priority authentication authentication encryption Diffie-Hellman duration
method algorithm algorithm group(seconds)
---------------------------------------------------------------------------
10 PRE_SHARED MD5 DES_CBC MODP_768 5000
default PRE_SHARED SHA DES_CBC MODP_768 86400
[H3CRouter]display ike proposal
priority authentication authentication encryption Diffie-Hellman duration
method algorithm algorithm group(seconds)
---------------------------------------------------------------------------
default PRE_SHARED SHA DES_CBC MODP_768 86400
可通過如下顯示信息查看到IKE協商成功后生成的兩個階段的SA。
[H3CRouter]display ike sa
total phase-1 SAs:1
connection-id peer flag phase doi
----------------------------------------------------------
1 219.140.142.211 RD|ST 1 IPSEC
2 219.140.142.211 RD|ST 2 IPSEC
flag meaning
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO—TIMEOUT RK-REKEY
IKE第二階段協商生成的IPsec SA用于保護子網10.1.1.0/24與子網10.1.2.0/24之間的數據流,可通過如下顯示信息查看。
[H3CRouter]display ipsec sa
===============================
Interface:Ethernet0/1
path MTU:1500
===============================
-----------------------------
IPsec policy name:"map1"
sequence number:10
acl version:ACL4
mode:isakmp
-----------------------------
PFS:N,DH group:none
tunnel:
local address:123.15.36.140
remote address:219.140.142.211
flow:
sour addr:172.18.253.0/255.255.255.0 port:0 protocol:IP
dest addr:192.168.2.0/255.255.255.0 port:0 protocol:IP
[inbound ESP SAs]
spi:0x3D6D3A62(1030568546)
transform:ESP-ENCRYPT-DES ESP-AUTH-SHA1
in use setting:Tunnel
connection id:1
sa duration(kilobytes/sec):1843200/3600
sa remaining duration(kilobytes/sec):1843199/3590
anti-replay detection:Enabled
anti-replay window size(counter based):32
udp encapsulation used for nat traversal:N
[outbound ESP SAs]
spi:0x553FAAE(89389742)
transform:ESP-ENCRYPT-DES ESP-AUTH-SHA1
in use setting:Tunnel
connection id:2
sa duration(kilobytes/sec):1843200/3600
sa remaining duration(kilobytes/sec):1843199/3590
anti-replay detection:Enabled
anti-replay window size(counter based):32
udp encapsulation used for nat traversal:N
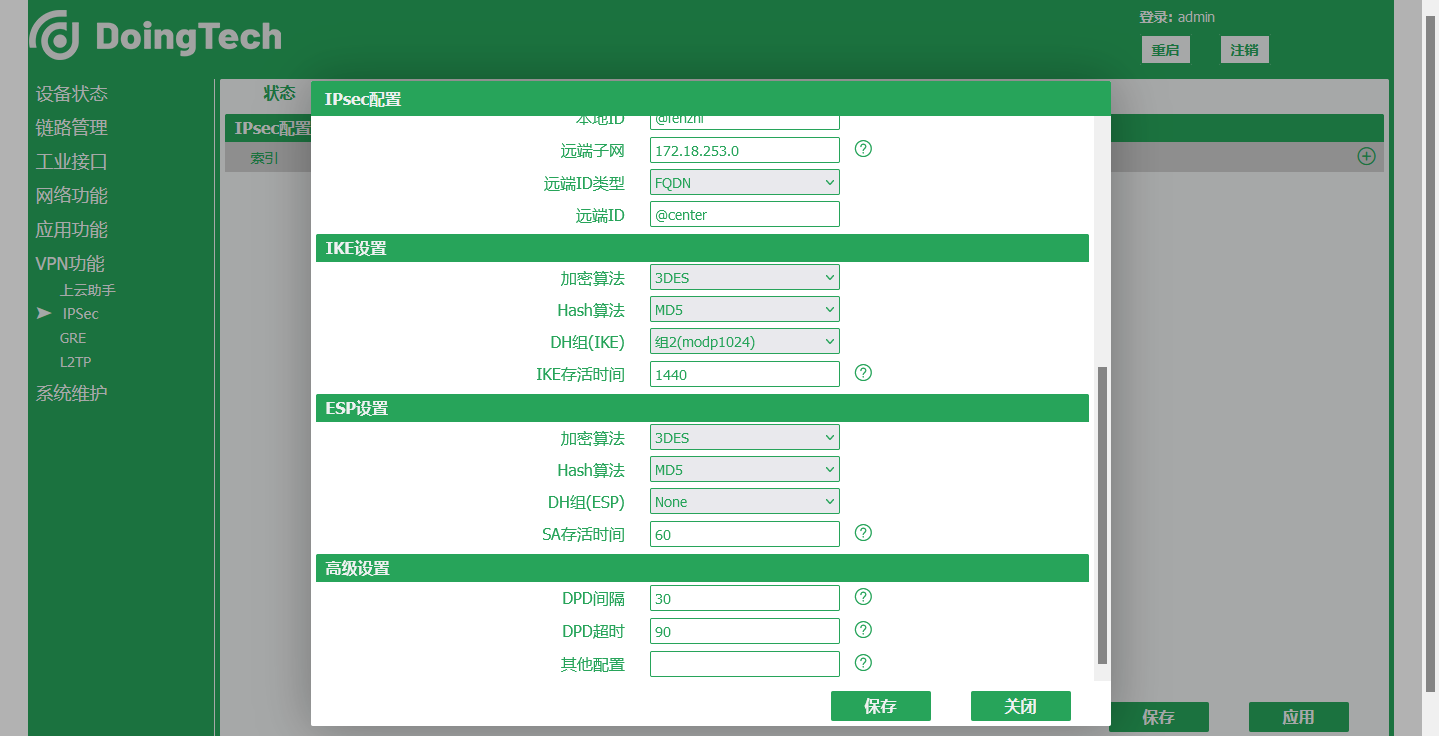
二、東用科技路由器IPSec VPN配置
● ORB305
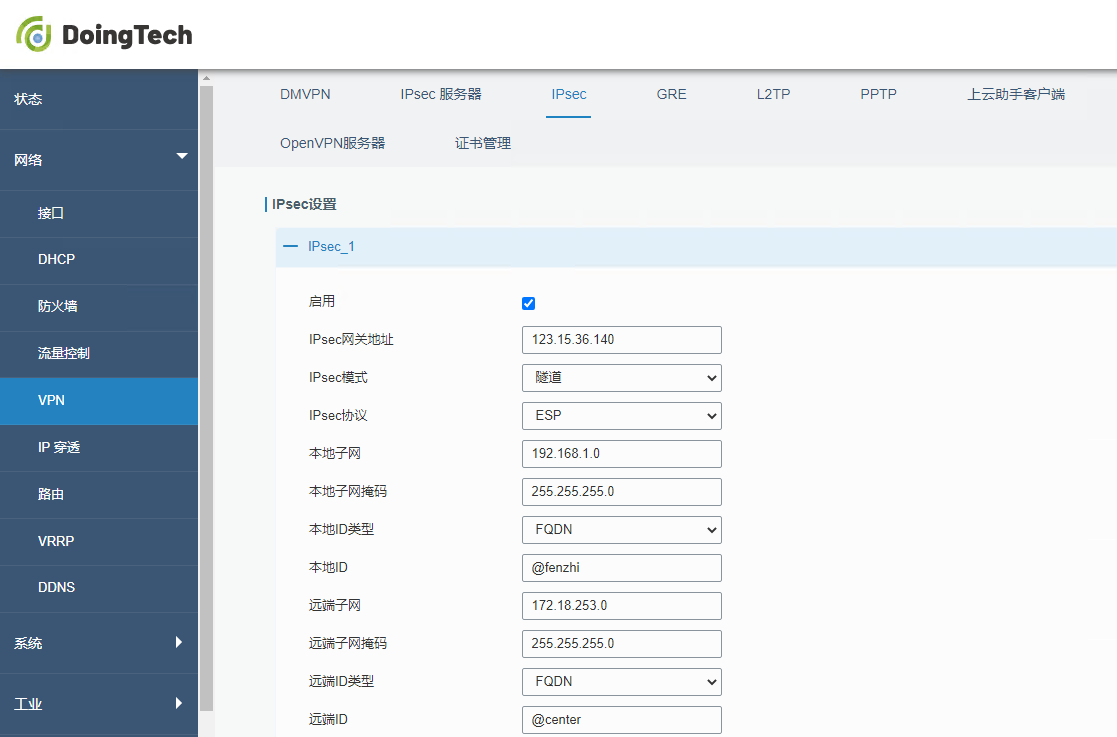
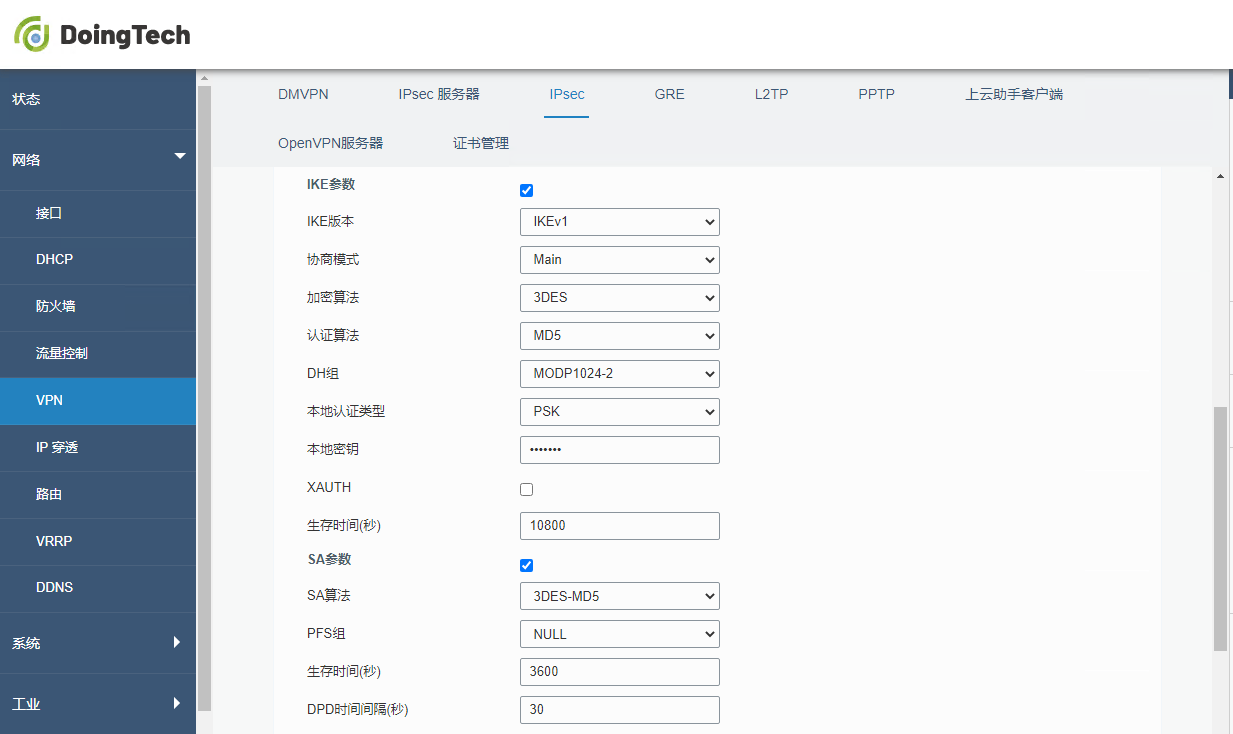
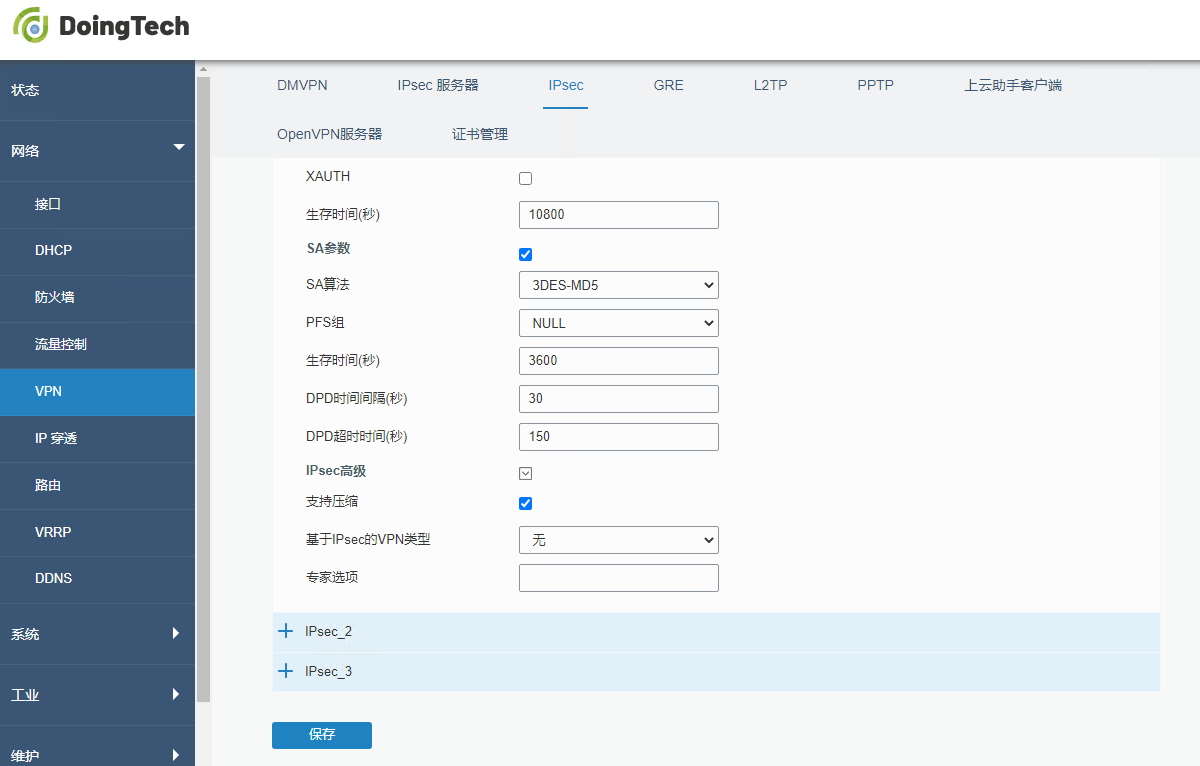
● ORB301
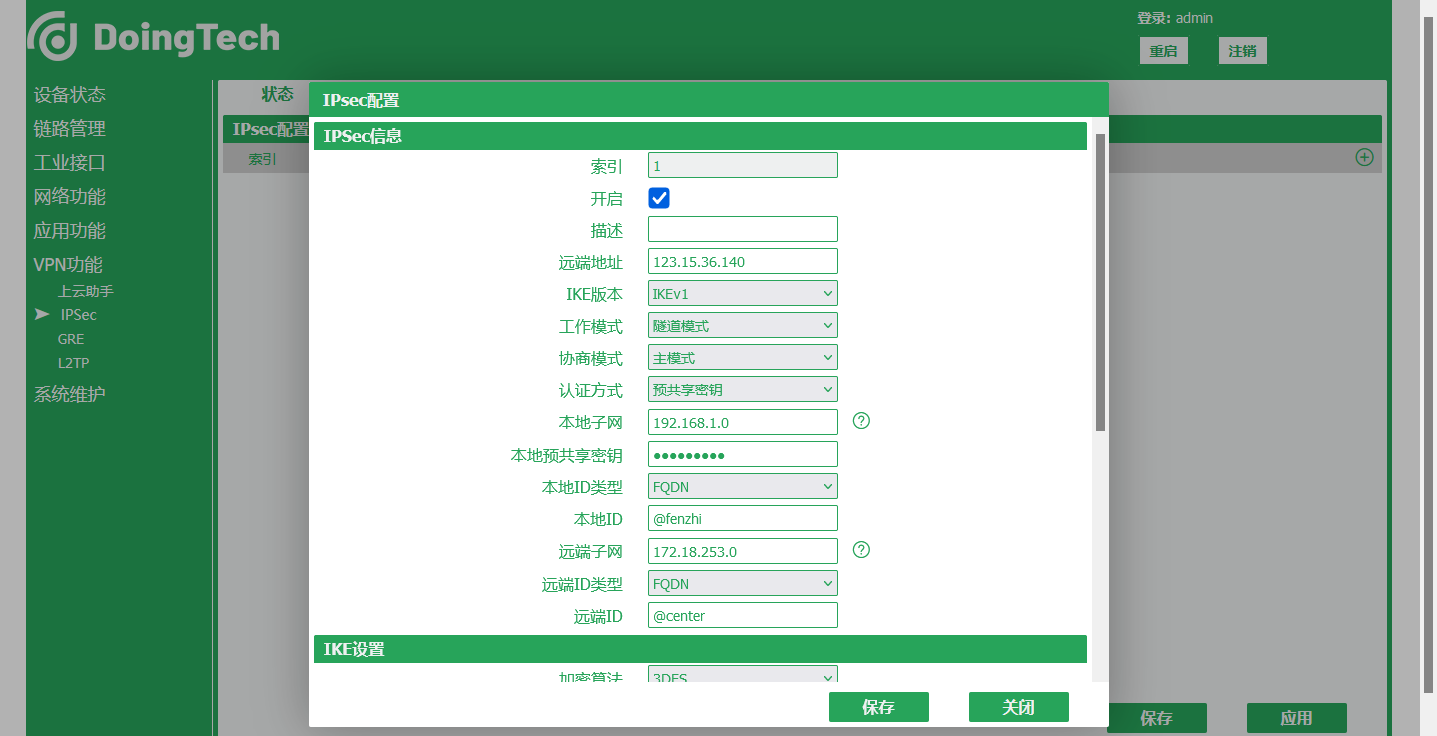
-
VPN
+關注
關注
4文章
297瀏覽量
30350 -
路由器
+關注
關注
22文章
3814瀏覽量
115997 -
IPSec
+關注
關注
0文章
59瀏覽量
23280
發布評論請先 登錄

















評論